As I poke around my home office, I find two wireless routers. Technically they should be a combo switch/router, or a L3 Switch, but they're here.
Well, one is the combo device, one is a flat out wireless router that would connect to an ISPs router to give us access to the internet.
So I hooked one up to my PC (My Laptop doesn't have Ethernet ports) so I could poke around again with my old-found (as opposed to new-found) IT knowledge.
Welcome to Routerworld.
It's not like Cisco's command line interface - This is for the consumer market, and that means you have to make things GUI-ish.
Hey, we may not use this anymore but that doesn't mean I want people to see the Key.
We weren't using WEP, but TKIP is only marginally better. There was some kind of odd disconnect if I recall correctly - Every device could use the higher security settings except my 2013 Macbook Air, so the compromise was made.
I should check what Authentication type our current setup is using.
Here is how an individual device would look; In this case, my Wii U.
I'm not sure what outbound port it would use, not 80.
The Wii U (and Switch) are P2P connected for playing Splatoon online.
Since the higher-ports are used for certain manufacturers (or just at random for connectivity), I *think* the Wii U had a port in the 4000s that one could tell their local firewall to leave open to have the game run smoother, but it normally boiled down to your internet speed, especially the upload speed.
Speaking of the Firewall;
Block ping is telling your firewall not to respond if someone pings it.
The alarming thing is, The Telnet box was checked!
Of course, that's if I initiated the connection, but I hope that even in the year 2016 people weren't allowing Telnet connections.
Oddly, SSH isn't a standalone option.
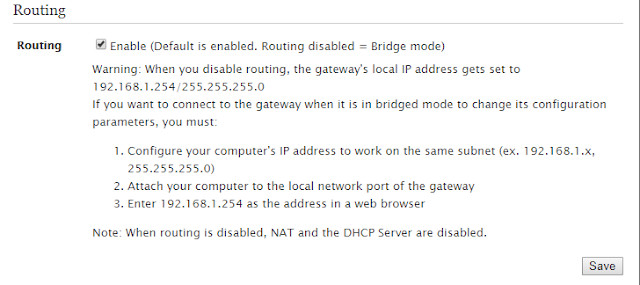
Bridge mode would be two computers talking to each other on the local network.
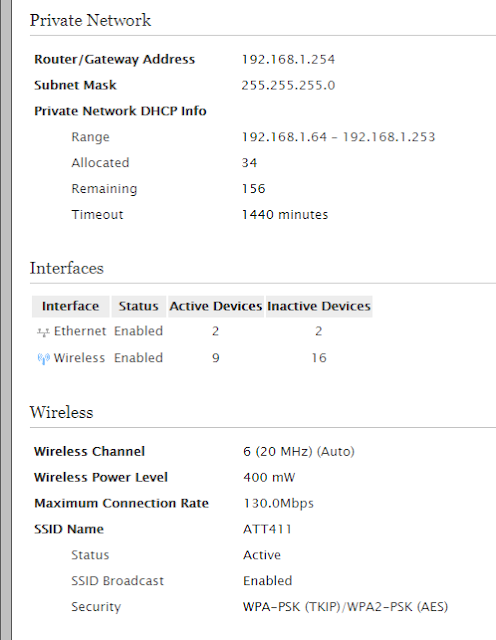
If your home network is using 190 devices, wow.
Ethernet enabled - My PC and either my phone (Charging, attached to my PC), or the Wireless adapter (Because I don't have a wireless card in this particular machine).
I have more reason to believe it's probably seeing the wireless adapter because it can see nine active devices on the Wireless side - probably various DirectTV cable boxes, maybe our router in use now.
Here are some logs;
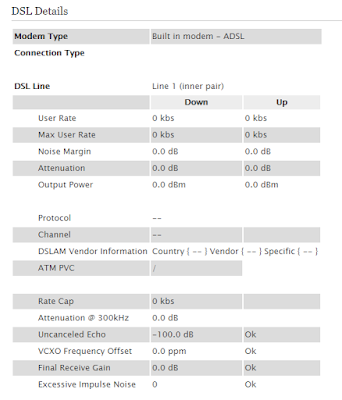
I leave you with some Digital Subscriber Line details. Nothing, because no internet service.
EMPLOYERS: This is me repurposing old technology.
Well, one is the combo device, one is a flat out wireless router that would connect to an ISPs router to give us access to the internet.
So I hooked one up to my PC (My Laptop doesn't have Ethernet ports) so I could poke around again with my old-found (as opposed to new-found) IT knowledge.
Welcome to Routerworld.
We own the equipment even though we don't have AT&T's internet anymore.
It's not like Cisco's command line interface - This is for the consumer market, and that means you have to make things GUI-ish.
Hey, we may not use this anymore but that doesn't mean I want people to see the Key.
We weren't using WEP, but TKIP is only marginally better. There was some kind of odd disconnect if I recall correctly - Every device could use the higher security settings except my 2013 Macbook Air, so the compromise was made.
I should check what Authentication type our current setup is using.
Here is how an individual device would look; In this case, my Wii U.
I'm not sure what outbound port it would use, not 80.
The Wii U (and Switch) are P2P connected for playing Splatoon online.
Since the higher-ports are used for certain manufacturers (or just at random for connectivity), I *think* the Wii U had a port in the 4000s that one could tell their local firewall to leave open to have the game run smoother, but it normally boiled down to your internet speed, especially the upload speed.
Speaking of the Firewall;
Block ping is telling your firewall not to respond if someone pings it.
The alarming thing is, The Telnet box was checked!
Of course, that's if I initiated the connection, but I hope that even in the year 2016 people weren't allowing Telnet connections.
Oddly, SSH isn't a standalone option.
Bridge mode would be two computers talking to each other on the local network.
If your home network is using 190 devices, wow.
Ethernet enabled - My PC and either my phone (Charging, attached to my PC), or the Wireless adapter (Because I don't have a wireless card in this particular machine).
I have more reason to believe it's probably seeing the wireless adapter because it can see nine active devices on the Wireless side - probably various DirectTV cable boxes, maybe our router in use now.
Here are some logs;
I leave you with some Digital Subscriber Line details. Nothing, because no internet service.
EMPLOYERS: This is me repurposing old technology.






Comments
Post a Comment